Microsoft Sso Setup
Did you know Azure Active Directory can provide Single Sign-On (SSO) to G-Suite (Google Apps)? In this blog, we will explore how to set this up from both the Azure AD side and also the G-Suite side.
- Microsoft Sso Setup Download
- Microsoft Sso Office 365
- Microsoft Sso Setup For Pc
- Microsoft Sso Setup For Windows 10
Click on the Microsoft Azure SSO App and then select Install to begin. Step one of the installation process simply provides an overview of how installing the Microsoft Azure SSO app will affect your Incident IQ installation. Select Continue once you are ready to proceed to step two.
Once SSO is configured, consider creating policies for Conditional Access to govern how G-Suite is accessed (e.g. only from a managed device, specific network, monitor for threats of the credentials such as for sale on the dark web, etc). For more information on G-Suite and Azure AD integration for SSO, see Tutorial: Azure Active Directory integration with G Suite
Note: SSO for up to 10 apps comes with the free version of AzureAD. For additional capability, P1 or P2 may be required. See Azure Active Directory pricing for more information.
- Hi all, I believe I have setup ADFS correctly so that SSO works correctly but just wanted to check the results. We have a W2008 R2 Domain on premise. Should it be the case.
- Sep 20, 2018 Detailed implementation guidance for single sign-on (SSO) is available in the Azure Active Directory (Azure AD) Help documentation. If you encounter a problem when you set up SSO by using that guidance, you can refer to this article. It provides a roadmap to help troubleshoot common problems with each setup.
Important: Chromebooks can sign-in with Azure AD credentials, see this video! (and here for more information)
Also Important: Once SSO is enabled in G-Suite only Azure AD credentials will be authorized and all legacy credentials (i.e. G-Suite credentials) will not be authorized for sign-in. If the user is using a Windows 10 device that is AADJ, then they will not need to type in their password to access G-Suite, SSO from Win 10 will automatically be available.
Let's begin!
Add G-Suite to Azure AD and configure it:
From within the Azure portal navigate to Azure Active Directory -> Enterprise Applications -> New Application and search for G Suite then click Add:
Once added, click Single Sign-on and click SAML
Edit the Basic SAML Configuration by clicking the pencil icon:
Configure using the following parameters:
Nitro pdf pro 10 serial.
Click Save. For User Attributes & Claims click the pencil icon:
Add a new claim:
Go back to the main SAML SSO configuration page, and download the base64 certificate for SAML Signing Certificate:
Copy the following URLs to a scratch pad, we'll use these to configure G-Suite:
Setup G-Suite for SSO:
See this article for more information on configuring G-Suite for SSO. From within G-Suite navigate to Admin –> Security -> Setup SSO. Paste the URLs you copied in the last step, into the SSO configuration, upload the certificate you downloaded previously, check the box for use a domain specific issuer and then click Save:
Assign the user to G Suite
Back in the Azure portal, click Users & Groups from within the G-Suite Enterprise Application:
Add a new user to G-Suite:
Checkout the different books links which we have mention below which will be used for the various exams also at the last we have given the link so that you can buy from this books. For any queries or questions feel free to ask below in comments.Download Free Tata McGraw Hill books PDF.  Download Free Tata McGraw Hill books PDFDownload Free Tata McGraw Hill books PDF (All Books) book covers all the section of books required for SSC, railway, UPSC, and various exams for General Studies section which are required for the exam. You can download this book PDF from the link provided below and start studying for the exams. You can download the books from the link provided below.
Download Free Tata McGraw Hill books PDFDownload Free Tata McGraw Hill books PDF (All Books) book covers all the section of books required for SSC, railway, UPSC, and various exams for General Studies section which are required for the exam. You can download this book PDF from the link provided below and start studying for the exams. You can download the books from the link provided below.
Turn on Provisioning:
Click on Provisioning and go through the steps on the blade. Starting with changing Provisioning Mode to Automatic.
Then click Authorize and type in your G-Suite credentials to go through the authorization process. Grant consent:
Back in the Azure portal, click Save to save your provisioning configuration. Once saved, you can opt to enable automatic synchronization of identities from Azure AD to G-Suite by clicking On for Provisioning Status:
Side bar, I could configure self service for end-users!
Back in G-Suite, you will notice the assigned users will start to sync:
Time to test!
I'm going to navigate to http://mail.google.com/a/soseman.org:
Notice this will redirect to Azure Active Directory:
Notice it challenges me for multi-factor authentication!
And I respond to the challenge using my Apple Watch 🙂
Once authenticated, accept the terms and conditions:
Microsoft Sso Setup Download
Now, I'm logged in and ready to use G-Suite!
Browsing to myapps.microsoft.com – G-Suite is added to the launcher!
Conclusion:
As you can see, configuring Single Sign On for G-Suite using Azure Active Directory is a rather easy and simple process – and probably can be completed within 15 minutes or less. Once configured, don't forget using Azure AD Conditional Access to govern how G-Suite is accessed, such as requiring a managed device (mobile or PC), monitoring the credentials for being compromised (impossible travel, up for sale on dark web, coming from atypical locations,etc), requiring MFA, and more!
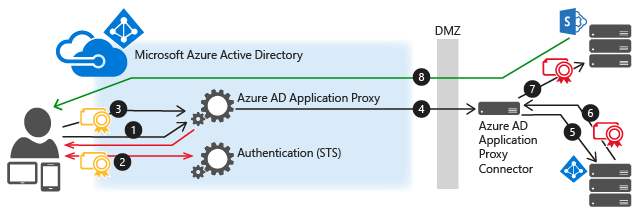
When you add a gallery app or a non-gallery web app to your Azure AD Enterprise Applications, one of the single sign-on options available to you is SAML-based single sign-on. Choose SAML whenever possible for applications that authenticate using one of the SAML protocols. With SAML single sign-on, Azure AD authenticates to the application by using the user's Azure AD account. Azure AD communicates the sign-on information to the application through a connection protocol. You can map users to specific application roles based on rules you define in your SAML claims. This article describes how to configure SAML-based single sign-on for a non-gallery app.
Note
Adding a gallery app? Find step-by-step setup instructions in the list of SaaS app tutorials
To configure SAML single sign-on for a non-gallery application without writing code, you need to have a subscription or Azure AD Premium and the application must support SAML 2.0. For more information about Azure AD versions, visit Azure AD pricing.
Before you begin
If the application hasn't been added to your Azure AD tenant, see Add a non-gallery app.
Step 1. Edit the Basic SAML Configuration
Sign in to the Azure portal as a cloud application admin, or an application admin for your Azure AD tenant.
Navigate to Azure Active Directory > Enterprise applications and select the application from the list.
- To search for the application, in the Application Type menu, select All applications, and then select Apply. Enter the name of the application in the search box, and then select the application from the results.
Under the Manage section, select Single sign-on.
Select SAML. The Set up Single Sign-On with SAML - Preview page appears.
To edit the basic SAML configuration options, select the Edit icon (a pencil) in the upper-right corner of the Basic SAML Configuration section.
Enter the following settings. You should get the values from the application vendor. You can manually enter the values or upload a metadata file to extract the value of the fields.
Basic SAML Configuration setting SP-Initiated idP-Initiated Description Identifier (Entity ID) Required for some apps Required for some apps Uniquely identifies the application. Azure AD sends the identifier to the application as the Audience parameter of the SAML token. The application is expected to validate it. This value also appears as the Entity ID in any SAML metadata provided by the application. You can find this value as the Issuer element in the AuthnRequest (SAML request) sent by the application. Reply URL Optional Required Specifies where the application expects to receive the SAML token. The reply URL is also referred to as the Assertion Consumer Service (ACS) URL. You can use the additional reply URL fields to specify multiple reply URLs. For example, you might need additional reply URLs for multiple subdomains. Or, for testing purposes you can specify multiple reply URLs (local host and public URLs) at one time. Sign-on URL Required Don't specify When a user opens this URL, the service provider redirects to Azure AD to authenticate and sign on the user. Azure AD uses the URL to start the application from Office 365 or the Azure AD Access Panel. When blank, Azure AD performs IdP-initiated sign-on when a user launches the application from Office 365, the Azure AD Access Panel, or the Azure AD SSO URL. Relay State Optional Optional Specifies to the application where to redirect the user after authentication is completed. Typically the value is a valid URL for the application. However, some applications use this field differently. For more information, ask the application vendor. Logout URL Optional Optional Used to send the SAML Logout responses back to the application.
For more information, see Single sign-on SAML protocol.
Microsoft Sso Office 365
Step 2. Configure User attributes and claims
When a user authenticates to the application, Azure AD issues the application a SAML token with information (or claims) about the user that uniquely identifies them. By default, this information includes the user's username, email address, first name, and last name. You might need to customize these claims if, for example, the application requires specific claim values or a Name format other than username. Requirements for gallery apps are described in the application-specific tutorials, or you can ask the application vendor. The general steps for configuring user attributes and claims are described below.
In the User Attributes and Claims section, select the Edit icon (a pencil) in the upper-right corner.
Verify the Name Identifier Value. The default value is user.principalname. The user identifier uniquely identifies each user within the application. For example, if the email address is both the username and the unique identifier, set the value to user.mail.
To modify the Name Identifier Value, select the Edit icon (a pencil) for the Name Identifier Value field. Make the appropriate changes to the identifier format and source, as needed. For details, see Editing NameId. Save the changes when you're done.
To configure group claims, select the Edit icon for the Groups returned in claim field. For details, see Configure group claims.
To add a claim, select Add new claim at the top of the page. Enter the Name and select the appropriate source. If you select the Attribute source, you'll need to choose the Source attribute you want to use. If you select the Translation source, you'll need to choose the Transformation and Parameter 1 you want to use. For details, see Adding application-specific claims. Save the changes when you're done.
Select Save. The new claim appears in the table.
Note
For additional ways to customize the SAML token from Azure AD to your application, see the following resources.
- To create custom roles via the Azure portal, see Configure role claims.
- To customize the claims via PowerShell, see Customize claims - PowerShell.
- To modify the application manifest to configure optional claims for your application, see Configure optional claims.
- To set token lifetime policies for refresh tokens, access tokens, session tokens, and ID tokens, see Configure token lifetimes. Or, to restrict authentication sessions via Azure AD Conditional Access, see authentication session management capabilities.
Step 3. Manage the SAML signing certificate
Azure AD uses a certificate to sign the SAML tokens it sends to the application. You need this certificate to set up the trust between Azure AD and the application. For details on the certificate format, see the application’s SAML documentation. For more information, see Manage certificates for federated single sign-on and Advanced certificate signing options in the SAML token.
From Azure AD, you can download the active certificate in Base64 or Raw format directly from the main Set up Single Sign-On with SAML page. Alternatively, you can get the active certificate by downloading the application metadata XML file or by using the App federation metadata URL. To view, create, or download your certificates (active or inactive), follow these steps.
Go to the SAML Signing Certificate section.
Verify the certificate has:
- The desired expiration date. You can configure the expiration date for up to three years into the future.
- A status of active for the desired certificate. If the status is Inactive, change the status to Active. To change the status, right-click the desired certificate's row and select Make certificate active.
- The correct signing option and algorithm.
- The correct notification email address(es). When the active certificate is near the expiration date, Azure AD sends a notification to the email address configured in this field.
To download the certificate, select one of the options for Base64 format, Raw format, or Federation Metadata XML. Azure AD also provides the App Federation Metadata Url where you can access the metadata specific to the application in the format
https://login.microsoftonline.com/<Directory ID>/federationmetadata/2007-06/federationmetadata.xml?appid=<Application ID>.To manage, create, or import a certificate, select the Edit icon (a pencil) in the upper-right corner of the SAML Signing Certificate section.
Take any of the following actions:
- To create a new certificate, select New Certificate, select the Expiration Date, and then select Save. To activate the certificate, select the context menu (..) and select Make certificate active.
- To upload a certificate with private key and pfx credentials, select Import Certificate and browse to the certificate. Enter the PFX Password, and then select Add.
- To configure advanced certificate signing options, use the following options. For descriptions of these options, see the Advanced certificate signing options article.
- In the Signing Option drop-down list, choose Sign SAML response, Sign SAML assertion, or Sign SAML response and assertion.
- In the Signing Algorithm drop-down list, choose SHA-1 or SHA-256.
- To notify additional people when the active certificate is near its expiration date, enter the email addresses in the Notification email addresses fields.
If you made changes, select Save at the top of the SAML Signing Certificate section.
Step 4. Set up the application to use Azure AD
The Set up <applicationName> section lists the values that need to be configured in the application so it will use Azure AD as a SAML identity provider. The required values vary according to the application. For details, see the application's SAML documentation. To find the documentation, go to the Set up <application name> heading and select View step-by-step instructions. The documentation appears in the Configure sign-on page. That page guides you in filling out the Login URL, Azure AD Identifier, and Logout URL values in the Set up <application name> heading.
Scroll down to the Set up <applicationName> section.
Copy the value from each row in this section as needed and follow the application-specific instructions for adding the value to the application. For gallery apps, you can view the documentation by selecting View step-by-step instructions.
- The Login URL and Logout URL values both resolve to the same endpoint, which is the SAML request-handling endpoint for your instance of Azure AD.
- The Azure AD Identifier is the value of the Issuer in the SAML token issued to the application.
When you've pasted all the values into the appropriate fields, select Save.
Step 5. Validate single sign-on
Once you've configured your application to use Azure AD as a SAML-based identity provider, you can test the settings to see if single sign-on works for your account.
Scroll to the Validate single sign-on with section.
Select Validate. The testing options appear.
Select Sign in as current user.
If sign-on is successful, you're ready to assign users and groups to your SAML application.If an error message appears, complete the following steps:
Microsoft Sso Setup For Pc
Copy and paste the specifics into the What does the error look like? box.
Select Get resolution guidance. The root cause and resolution guidance appear. In this example, the user wasn't assigned to the application.
Read the resolution guidance and then, if possible, fix the issue.
Run the test again until it completes successfully.
For more information, see Debug SAML-based single sign-on to applications in Azure Active Directory.